- How is Ransomware Attack Administered?
- Phishing Emails-
- Typo-Squatting-
- Spear-Phishing-
- Physical Attacks-
- Ways to Mitigate Ransomware Attacks
- 1). Ensure That Your Devices are Patched
- 2). Perform Regular Data Backups and Recovery
- 3). Implement an IDS
- 4). Utilize Endpoint Security
- 5). Filter Email Contents
- 6). Two-Factor Authentication
- 7). Have a Penetration Testing
- Summary: Effective Ways to Mitigate Ransomware Attacks
- Conclusion
You’ve heard of the latest ransomware attack that spread across Europe, taking down multiple organizations. Unfortunately, these attacks will continue to get bigger and more frequent as cyber criminals look for more vulnerable victims. If you are a small business owner who occasionally uses the internet to communicate with clients or store information on your website, you should not feel helpless. Here are some ways that you can mitigate ransomware attacks, whether you have been personally attacked or wish to be more prepared in the future.

If you own a business or are a part of the IT department of a company, you have probably experienced or heard about ransomware attacks and their repercussions. Ransomware is basically a type of malware that prevents access to a file, system, or even a device until a ransom is paid; hence the name ransomware.
When this happens, recovery is extremely difficult and the attack just usually needs seconds before blocking users from important and sensitive data. Imagine the effect of ransomware attacks especially on organizations, businesses and the government.
Basically, ransomware attacks abuse the use of encryption. It just needs to install a malicious code to infect your system then it instantly begins encrypting your hard drive preventing you from accessing some important and sensitive data.
How is Ransomware Attack Administered?
Here is how Cybercriminals administer ransomware attacks:
Phishing Emails-
Most successful ransomware attacks are administered by email phishing. It involves coercing people into clicking malicious links or attachments without them knowing that it can distribute ransomware
Typo-Squatting-
This happens when you enter a domain that is similar to frequent domains that users enter. It usually asks for sensitive information or it can ask you to download malicious files that can access data even if it has encryption.
Spear-Phishing-
This is another phishing campaign done by cybercriminals wherein they impersonate key individuals of an organization, making it harder for users to detect.
Physical Attacks-
Attacks can be easily transferred by simply using infected flash drives.

Ways to Mitigate Ransomware Attacks
Now that you know what a ransomware attack is and how it is administered, it is now time to know how to protect yourself from being a victim.
The best way to mitigating cyber-attacks is by practicing and utilizing cyber hygiene. Here are some ways to prevent yourself and lower the possibility of getting your hard drive attacked.
1). Ensure That Your Devices are Patched
Check that all your systems and servers are up to date and are using the latest patch. You can find the latest updates by visiting these sites:
For Windows: https://support.microsoft.com/en-us/windows/update-windows-3c5ae7fc-9fb6-9af1-1984-b5e0412c556a
For Mac: https://support.apple.com/en-us/HT201222
2). Perform Regular Data Backups and Recovery
Although this doesn’t prevent you from getting attacked by malicious software, backup is important in preventing a greater impact on your organization or business. Always monitor and test your data backup and system recovery to make sure that it works perfectly. You can work with MSSP or MSP in creating the protection plan you want for your system.
3). Implement an IDS
An IDS or Intrusion Detection System compares network traffic logs to detect any malicious activity. When you have this system in place, you will be quickly alerted about any malicious activity and this will help you act in good time.
4). Utilize Endpoint Security
Switch to endpoint security since it utilizes MLAI in catching attacks, which anti-virus software can mix. It is always beneficial to invest in the latest protection as much as possible.
5). Filter Email Contents
This is usually provided by email providers such as Gmail. This automatically sorts spam and phishing emails and removes them from your primary inbox.
6). Two-Factor Authentication
Two-factor authentication is usually done by organizations and businesses in their email accounts. This can reduce the risk of an employee’s email getting hacked. It also helps to prevent hackers from obtaining personal information that can be used in distributing ransomware attacks inside the organization. This is usually free on most email providers.
- To do this, open your Google account then select Security on the left side panel.
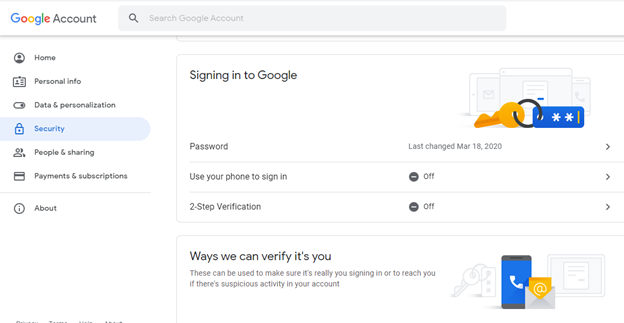
- Then look for signing in to Google and click the 2-step verification under it. After doing so, do all the needed setup. You can add more than one type of verification such as text message, backup codes, security key, etc.
7). Have a Penetration Testing
Another way to make sure that your system is safe from getting attack is through penetration testing. This works by involving a third party to attempt breaching your system security and check if there are vulnerable spots in it. This will help you to identify the system’s weakness before cybercriminals do. So, make sure to do this regularly.
Summary: Effective Ways to Mitigate Ransomware Attacks
- Backup data (Air gap)
- Update your operating system
- Keep your applications up to date
- Install the latest patches for your operating system and other software
- Disable unnecessary services, such as SMBv1, on all servers and workstations
- Enable Point-to-Point Tunneling Protocol (PPTP) filtering on your firewall
- Configure Windows Firewall properly on all servers and clients
- Turn off email auto preview in Microsoft Outlook, as well as automatic opening/execution of file attachments. Disable macros in Office documents by default. Deploy Office Viewer software to open DOCX, XLSX and PPTX files safely.
- Block untrusted websites, especially pornographic websites. Disable or isolate untrusted web browsers that cannot filter malicious JavaScript or advertisement pop-up windows.
- Use an automated patch management solution to automate the application of patches for the latest version of common third party software such as Adobe Flash, Java and Adobe Reader. Remember to block older versions of these products from being installed.
- Takeaway: Ransomware attacks can be mitigated by following a few guidelines.
Conclusion
We hope that any of the aforementioned methods will prove useful to help you curb ransomware attacks. You can use more than one of these methods to tighten your security against these attacks.