You might think that the only people that care about botnets these days are those looking to make some extra cash or the government trying to find terrorists. However, even if you don’t live in the US, and you're not anti-American, botnets still can cause problems for you. You see, if someone in the US has a botnet that uses your company's computers as one of its members, they can cause a lot of trouble for your site. In this article I'm going to show you how to find a botnet on your network at home or at work using Windows 7.
The word Botnet has been derived from two words network and robot. It is also called the “Zombie Army.” The bot can be considered as a device that is corrupted by malicious code. A single attacker or group of attackers controls this bot. The bot starts its action by becoming a part of any network and harms the network. This is how Botnet works.
The primary purpose of the Botnet is to infect internet-connected devices. It remains hidden to the user of the device as it uses considerable computing power. One typical example of the Botnet is “Ad Fraud Botnet.” In this guide, the methods of finding a botnet on your network will be discussed. You will also learn how you can prevent and destroy them.
Downloading the Software RUBotted
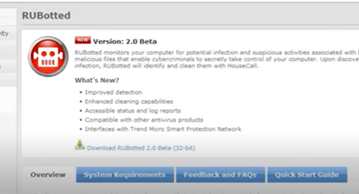
RUBotted software is used for monitoring any suspicious activity related to your computer. This software helps to detect and remove the Botnet on your network. For that:
- Download the software from the given link.
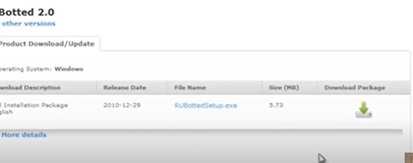
- After finishing downloading, run the program.
- Hit the “Next” button.
- Check the “I accept the agreement” button and hit “Next.”
- Click on the “Install” button.
Installing the Software
Now, a new window will appear. There:
- Hit the “Next” button.
- Select “I Agree” and then “Install.”
- Click on the “Finish” button.
After finishing the installation
- Open the main interface of the software.
- Look at the current status.
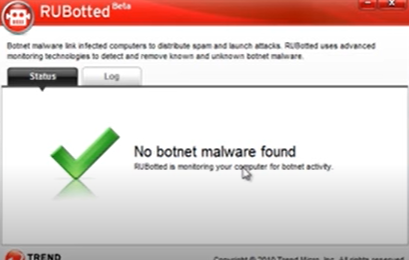
RUBotted is a helpful software for finding Botnets on your network. You can download this software for free and easily install it.
What is the Attacking Process of Botnet Network?
- The attacker or group uses some specific “Trojan viruses” to get access to their targeted devices.
- Then they try to assault the mechanism of the computer’s security system.
In this process, they enable huge-scale destructive functionality. There are multiple types of botnet attacks. Such as:
- DDOS. The full abbreviation of this term is Distributed Denial of service. This botnet attack causes unplanned downtime of any application.
- Credential- Stuffing attacks that cause account takeovers.
What are the most dangerous Botnet Attacks?
ZEUS
- This botnet attack infected over 13 million computers.
- This is a “Banking Trojan” Category.
- The life span of this Botnet is 2007-2021.
Storm
- Almost 2 Million Computers were attacked.
- Life span was 2007- 2008.
- The category of this attack is email worm for DDoS and Spam.
Mirai
- The distribution of this attack is brute-force attacks.
- Its life span is 2016- present days.
- This is a DDoS botnet category.
- It has infected over 5 million computers.
3ve
- This is a click fraud botnet category.
- It attacked over 2 million devices.
- It was distributed through social engineering.
- The financial impact is over 30 million dollars.
Mariposa
- This is a Trojan category botnet attack.
- The life span is from 2009 to 2011.
- It infected over 33 million computers.
- It is distributed through USB thumb drives, p2p networks, pirated software, etc.
- This Botnet attacked about 190 countries’ users.
Summary: Find a Botnet on your Network
- Investigate the traffic to and from your public-facing servers on port 80 and 443.
- Identify the source of the traffic.
- Investigate.
- Check your DNS servers.
- Monitor traffic patterns.
- Look for unusual spikes or drops in traffic or bandwidth usage.
- Look for unexpected spikes in your outgoing email counter.
- Watch for unusual activity from your domain name registrar, web host, or DNS host due to compromised passwords or unauthorized password changes.
- Check your website logs for malicious scripts or activity (e.g., SQL injection attempts).