Endpoint protection solutions are critical in today's networked environment. Although the importance of endpoint protection is high, so is the degree of confusion surrounding it. Maybe you're asking yourself, "What does Symantec endpoint protection do?" In an effort to help clarify this question, we've put together an educational series about Symantec endpoint security solutions.

Symantec endpoint protection is computer security software with a combination of firewall, intrusion prevention, and anti-malware features for protecting desktop computers and servers.
The software combines other features such as proactive threat scanning, group update provider, domains, SQL database support, and location awareness. It is, therefore, a hybrid form of a security system.
However, many people use SEP without the knowledge of how it works. Here is a comprehensive explanation of what Symantec does.
Attacks Protected by Symantec Endpoint Protection
Since Symantec EP has several defense layers against threats, it can protect the computer or server against known and unknown attacks. The approach used by this software is to protect the computer network before, during, and after the attack.
Therefore, the software has several tools that ensure your computer network is secure before the attack. The protection occurs in four phases, as explained below:
1). Incursion Phase
During this phase, hackers or malicious individuals break into the network using target attacks like targeted malware, zero-day vulnerabilities, social engineering, and SQL injection. Therefore, SEP protects the network before it is attacked using these technologies:
- Firewall or Intrusion prevention
This feature analyzes incoming and outgoing traffic and then blocks the threats before they are executed on the computer. The firewall offers protection against web-based threats.
- Application control
This feature controls access to files and registry and how the various processes are allowed to run.
- Device control
This feature limits access to a particular hardware and controls the devices that can download or upload information.
Other SEP protection features include memory exploit mitigation and network traffic mitigation.
2). Infection Phase
In the infection phase, hackers break into the computer network using SQL injection, social engineering, and targeted malware, among others. Therefore SEP launches some technologies to detect and prevent such attacks before they infect the system.
These SEP technologies for infection prevention include memory exploit mitigation, high-speed emulation, behavioral monitoring (SONAR), and anti rust file protection. The combination of these protection strategies neutralizes the attack before it affects your computer network system.
3). Infestation and Exfiltration
During this phase, the computer system has already been affected, and exfiltration has taken place. Intruders may have stolen intellectual property or transferred data from the computer without authority.
Therefore, Symantec endpoint protection initiates two protection strategies to prevent further action by the intruders. These strategies are behavioral monitoring and firewall or intrusion prevention to block the threats from traveling through the network and avoid the infection's spread.
4). Remediation and Inoculation
SEP launches its agent and single console in the final protection phase that protects platforms, operating systems, and businesses. This phase's protection strategies include host integrity, power eraser, system lockdown, and EDR console integration.
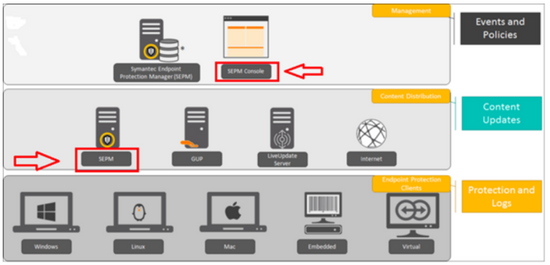
The simplified architecture of the Symantec endpoint protection and its operation is as shown below.:
Depending on the computer model you are using, you can install the appropriate version of the protection software. You can try Folder lock version 7 to ensure maximum protection of your folders, encrypted files, external drive, and many more.
How to Check the Status of Protection in Your Computer?
You can check whether the network is protected by SEP protection. Here are the steps how:
- Right-click on the SEP icon on the left side of the taskbar.
- Then click the "Open Symantec Endpoint Protection" option.
- Allow it to open by selecting "Yes" on the dialog box that will appear.
- Then click on the "Help" icon on the top-left corner and select the "About" option.
- A new window will appear with the protection status information.
Summary: What Does Symantec Endpoint Protection Do?
- Symantec Endpoint Protection (SEP) protects your Windows computers against viruses, malware and other malicious threats by analyzing all parts of the computer and determining if a file is dangerous.
- As computers and laptops are increasingly used in businesses to conduct work and share information, cyber attacks using viruses, worms and Trojan horses have become more complex and damaging.
- The software uses a combination of machine learning, artificial intelligence, advanced threat detection engines, behavior monitoring and other technologies to defend against attacks.
- The SONAR engine monitors your system in real time to evaluate suspicious files and applications.
- It compares their behavior with the behavior of known malware and also looks for deviations from what is normal for a “good” file or application in your computer environment.
- If a threat is detected, you are notified on your screen as well as an alarm in the console with severity information about the issue.
- If a threat affects multiple computers on your network, you can view the status of each computer from the console and take action on any alarms or threats.
- Symantec Endpoint Protection is enterprise security software that protects remote devices from viruses, malware and other.
Final Thoughts
Symantec Endpoint Protection is a hybrid version of computer network protection software that combines multiple protection features. However, some users do not understand how it works. The above guide will help you understand what SEP does on your computer.